Maurice Worm: The world's first cyber attack
 |
| Maurice Worm: The world's first cyber attack |
November 3, 1988, Hands-on the heads of US military defense officials. Their computers have been slow since morning for some unknown reason. They are not able to check any mail, some strange kind of log message is coming when you click on the mail button. Their technical engineers are watching the matter, but they can't do anything. They have already received news that NASA's Jet Propulsion Laboratory has been shut down for some time, their system is not working, their computers are slow and they are showing some error messages. NASA employees have started unplugging their computers for fear of data theft.
Even educational institutions like Harvard and Princeton University are suffering from the same problem. The same problem everywhere! Surely someone is planning to make the internet system useless. Military defense officials mistakenly believe that they may soon face a military attack. Very quickly they also started unplugging their computers.
The whole internet system is on the way down. A group of University of California programmers hurried down to solve the problem. After 24 hours of tireless work, they discovered that the condition was caused by a computer worm. The worm is being transferred from one computer to another very quickly. But this worm was a little different from all the other worms of that time.
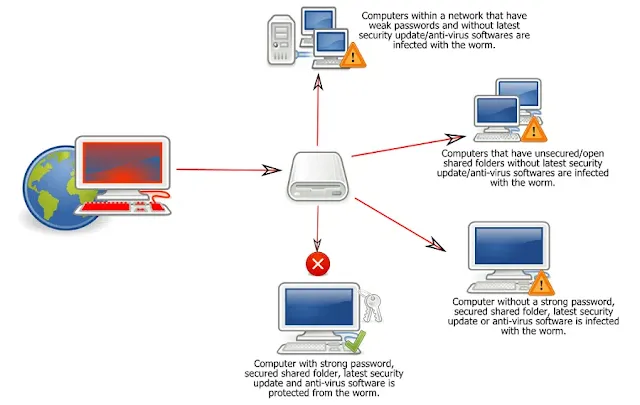 |
| The way a computer worm spreads from system to system |
Typically any cyberattack, in particular, is a feature of computer worms that first try to find a backdoor or weakness in the system. Then he enters the system and the computer through that backdoor and performs his work and tries to go inside another computer. In this way, the worms spread themselves on the Internet, creating countless copies of themselves, and at the same time accomplishing the immoral purposes for which they were created.
Maurice Worm followed almost the same policy. The worm was basically attacking computers with a kind of Unix operating system . Worms were entering the system through a backdoor of the then Unix mail delivery software (Sendmail). But over time, that is likely to be the case with VAX and Sun Microsystems systems. However, Maurice worms are not exactly like the common worms that are made for some malicious work. Rather, the worm was more prone to how to quickly find the backdoor and move from one system to another.
So the question is - if Maurice Worm doesn't do anything immoral, then why would the internet be useless? The reason for this is basically the same - the exceptional behavior of Maurice Worm.
Another common feature of computer worms is that if a worm already exists in a system, no copy of that worm will re-enter that system. If for some reason the pre-existing worm is no longer present in the memory, only then can a copy of the worm enter the system.
But Maurice Worm is an exception. On average, a copy of the worm will re-enter any one of the seven infected computers - following the possibility that the worm was working. The situation was that there were many copies of the same worm program on the same computer, each doing the same thing over and over again, causing the CPU memory to be filled with countless copies of that program. As a result, the system was slowly slowing down and the internet system was becoming useless. According to security experts, the average worm would not have spread so fast if an average of 6,000 had been used instead of every seven.
 |
| Cyber Security |
Eventually, a team of programmers from the University of California was able to come up with a 'temporary solution'. Temporarily because it does not completely remove the worm from the system but stops the tendency of the worm to migrate rapidly.
The panic of the Morris Worm could be stopped within 24 hours, but it has caused a lot of damage. Although the Internet was not as widespread then as it is now, there were approximately 60,000 computers connected. Yet about 10% of the entire Internet is useless. According to the U.S. General Accounting Office, about 1 million to 10 million in assets have been lost, with some organizations deleting data from servers for fear of their data being smuggled, as well as disrupting military and university operations.
A week passed to see. Despite thousands of efforts by security experts, the main programmer of the worm has not yet been caught. Although there were some minor cybercrimes before, they were confined to a specific organization, never before on such a large scale. So this time the police were also looking for the accused. There is a kind of curiosity even among the common people. The first cybercrime law was introduced in the United States in 1986. But no one has been punished under this law yet. So there is a kind of tension in everyone.
At that moment, a phone call came to the New York Times office. One reporter picked up the phone.
From the other end, it was said,
- Hello, is this the New York Times?
- Guys ...
- Well, I know about that worm programmer. But the fact that he did this is actually a harmless experiment. It was not intended to cause any harm.
- What's her name?
- It is not possible to say the name. What is the punishment for such crimes?
- Look, I have no idea about this. The incident is also new to me. If he pleads guilty in his name, the sentence may be reduced.
This goes on for quite some time. The reporter kept trying to find out the name and address; Meanwhile, the man on the other side is also stubborn, he will not say his name at all, he is more interested to know about the law and punishment of cybercrime.
After talking for a while, the answer finally came from the other end, “ His name is RTM. He hung up the phone.
Later, at the initiative of the reporter and with the help of National Security, it was possible to find out the full extent of RTM - Robert Tappan Morris, who was then an undergraduate student at Cornell University. He was immediately arrested.
The FBI later said in a statement that the worm was "distributed around 8.30 pm on November 2, 1988." To avoid everyone's suspicion, Robert Morris hacked a computer at MIT and uploaded the worm from there. "
 |
| Robert Tappan Morris |
According to Robert Morris, he uploaded the worm only to measure the extent of the Internet. For this reason, the worm could only make its own copy and move from one system to another, without doing anything immoral. If a system blocks his worm, he has coded it to allow worms to enter the infected computer to avoid this problem. But he could not have imagined that the worm would spread so fast. By the time he realized it was too late. He pleads guilty to two of his friends. One of the two later called the New York Times office.
He was fined 10,500, and 400 hours of community service, and three years in prison under the then-Cyber Act for lack of evidence against him. He is currently serving as a faculty member at MIT.
It's been 32 years since the Maurice Worm Attack. In the meantime, many more big cyber crimes have been organized, maybe more in the future. That is why security experts are fighting against them day and night. But Maurice Worm's role as one of the first major cybercrimes.







lovely info about cyber attack
I try my best. Thanks for your comment.