7 Common Types of Cyber Attacks and Their Remedies
 |
| Types and remedies for Cyber-attacks |
Suddenly the mobile rang in the middle of the work, the message came. It says that the customer has to win a large sum of money and click on the link next to get it. The insidious hacker got full control of the mobile phone as soon as he clicked on the link believing the customer's message.
Such incidents are happening all over the world. As soon as the word hacker was heard, a negative feeling arose in everyone. Ethical hackers emerged to eradicate cybercrime and punish these hackers. Those who knit them are skilled and determined to cut all the illegal nets. However, there are more hackers in the world than ethical hackers. Because many young people get involved in the world of crime by going for hacking as a hobby. Every year, many organizations have lost billions of dollars just because of this crime. Even people are being bullied.
However, it has been possible to eliminate all the harmful effects of ethical hackers. They are trying to find a solution to the problem of cyber attacks so that they do not have to suffer many losses. They are researching the process by which cyber attacks can be carried out and how to prevent them. Let us know about the type of cyber attack and its remedy.
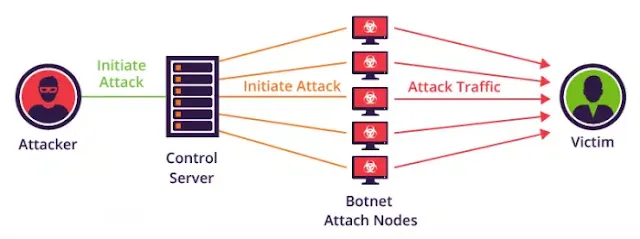
1) Botnet
Remedy
Emails from untrusted sources or emails from spam boxes cannot be opened. If there is a link in the email, you have to verify it first, then you have to work on it.2) Distributed Denial of Service (DDOS)
Remedy
Using powerful paid anti-virus. Installing firewalls and restricting traffic to and from devices or servers. Emails received from untrusted sources are not open. Don't open emails from strangers and be wary of acquaintances.3) Malware:
Remedy
Do not download any software from untrusted websites. Please read the terms and conditions carefully before installing any software. Update the software you use regularly, but refrain from doing any security updates through pop-ups.4) Phishing
 |
| Phishing |
Remedy
Beware of buying anything online, applying for a job, providing passwords, and providing personal information. If you see any tempting offer or price, check first and then work.5) Ransomware
Remedy
Do not pay the ransom. These threats are used by hackers to intimidate you. Even if you submit a payment, there is no guarantee that you will regain access to your system. If your computer is infected (e.g., you can't access your computer, or your files are encrypted), contact a reputable computer technician or specialist to find out if your computer can be repaired and your data restored. Be sure to back up your data regularly via external storage drives to minimize the effects of a ransomware infection. Your files may be unexpected, but it is important to have an up-to-date backup.6) Spyware
 |
| Spyware |
Remedy
Refrain from using all types of unverified links. Don't surf porn websites. Because it is on most websites, the device will be hacked as soon as you click on a picture or video.7) Virus
Remedy
Once a computer is infected with a virus, it is dangerous to use it without reinstalling the operating system. However, there are several ways to repair a virus-infected computer. These methods depend on the type of virus and the degree of infection. Need to use anti-virus. If a computer has a virus that cannot be removed by anti-virus software, a reinstall of the operating system may be necessary. To do this, you need to delete the hard drive completely (you need to delete and format the partition).Read more:
- This way, you are destroying your own laptop!
- How do Fingerprint Scanners Work on Phones?
- Does UPS really protect the Computer?
We hope you find this post useful. Did you know this information before? There was an invitation to comment!